The process is pretty much straight forward with some caveats that I’ll explain below.
First I moved the Data/Migrations and Models folder out of my web app into to my new project (figure 1). I got an unexpected compile error - it was a rather obscure error from the _LoginPartial.cshtml.gs.s file – which is the compiled file. To resolve this I had to update the _LoginPartial.cshtml manually since intellisense was not working in this file (figure 2). Once I did that, and updated namespaces for the existing ApplicationUser references, my web app was compiling and running again.
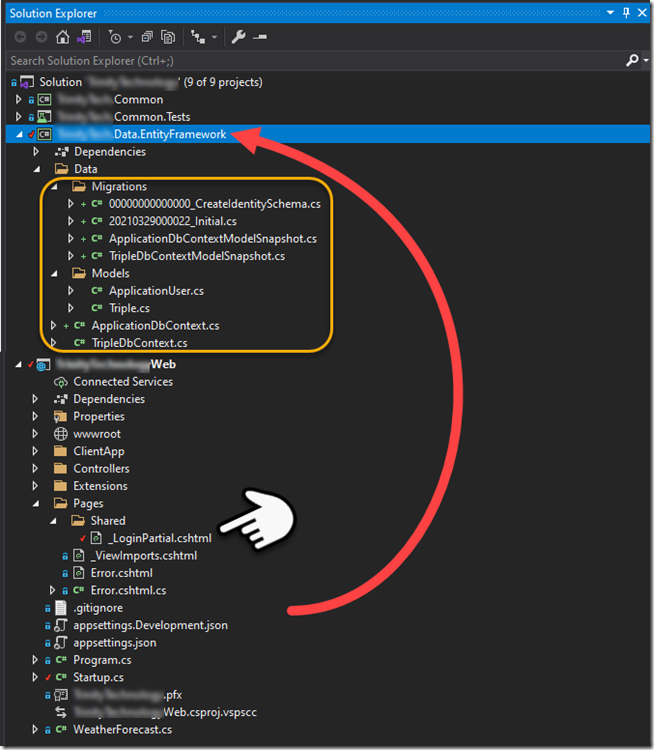
Figure 1
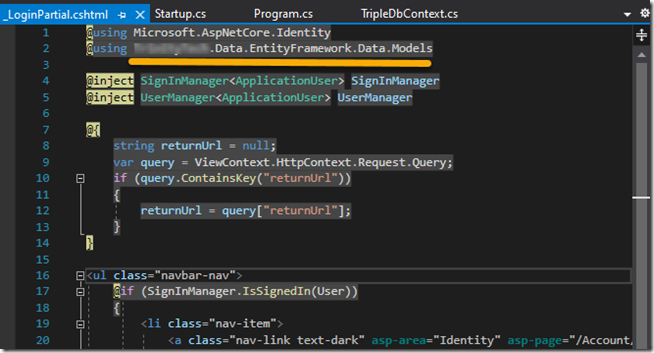
Figure 2
I created my new TripleDbContext as well as the Triple table (see figure 1). I then added the code pointed to below so that my new TripleDbContext will have a connection string when needed.
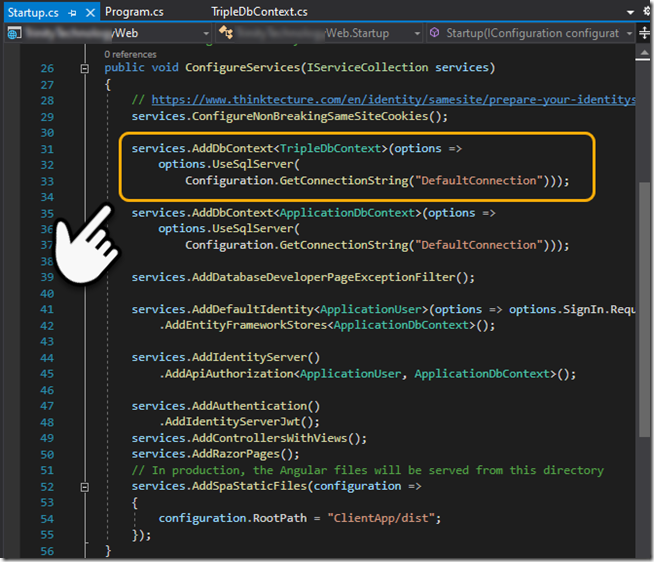
Figure 3
If you don’t have the dotnet –ef tool installed you can go to the root of your web app [command prompt] and type the following:
dotnet tool install --global dotnet-ef
After installed you’ll need need to switch to the “project that contains your xxxDbContext” and use the following command line. Since we have more than one context, e.g., ApplicationDbContext (security) and TripleDbContext (new) we have to provide the –context or it will complain, likewise we have to specify the DbContextOptions<TripleDbContext> in the constructor for options (see figure 4).
dotnet ef migrations add "Initial" -o "Data/Migrations" --context TripleDbContext
dotnet ef database update --context TripleDbContext
Note that I provide the connection string for the OnConfiguring() function from the environment – this will only be needed when configuring the database, e.g., doing the two commands above.
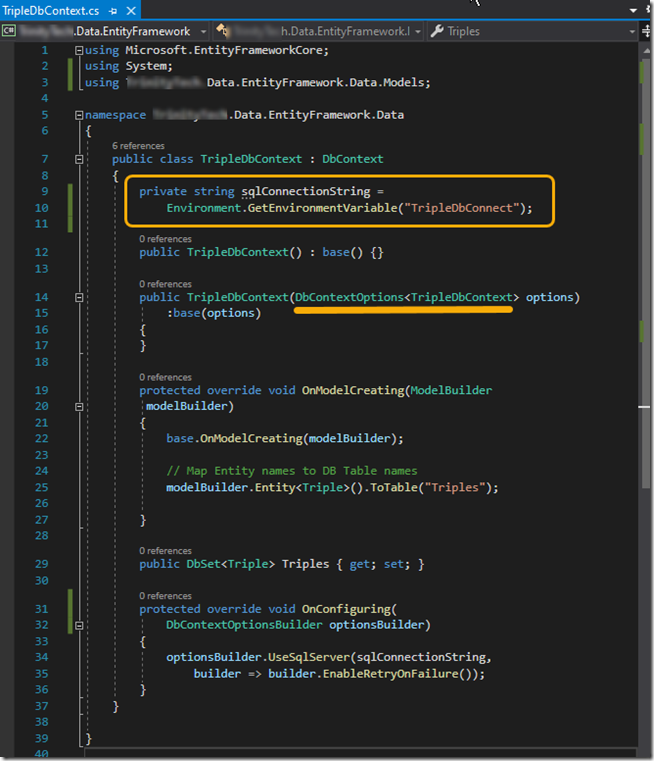
Figure 4
With that you’ll find your database has the new database table.
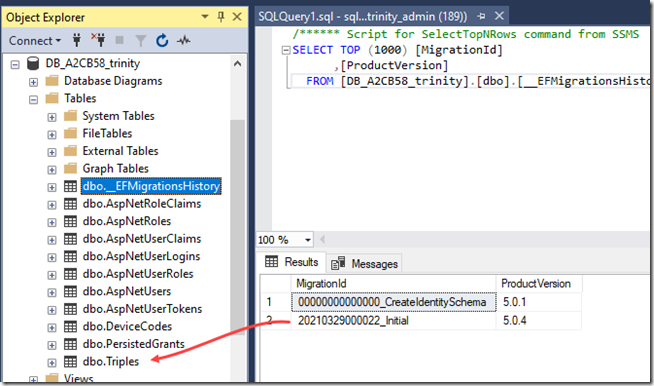
Figure 5
500 error when deployed
Object reference not set to an instance of an object.
Problem Id:
System.NullReferenceException at Microsoft.Extensions.DependencyInjection.IdentityServerBuilderConfigurationExtensions+<>c.<AddSigningCredentials>b__10_2
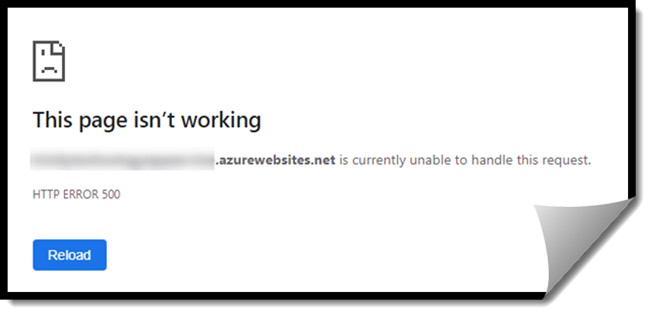
This can be tough to diagnose if you are not deployed to Azure [with application insights enabled]. With app insights the message is not real helpful, but a clue lies in the “identityServerBuildConfigurationExtension”
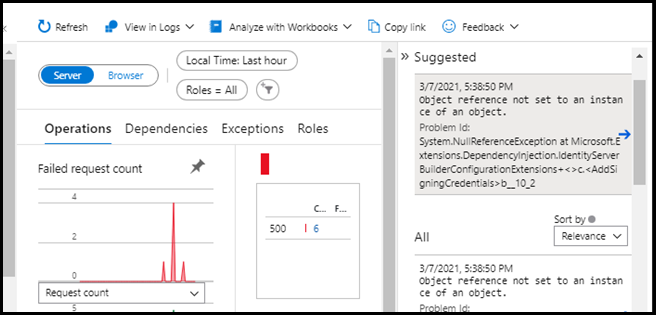
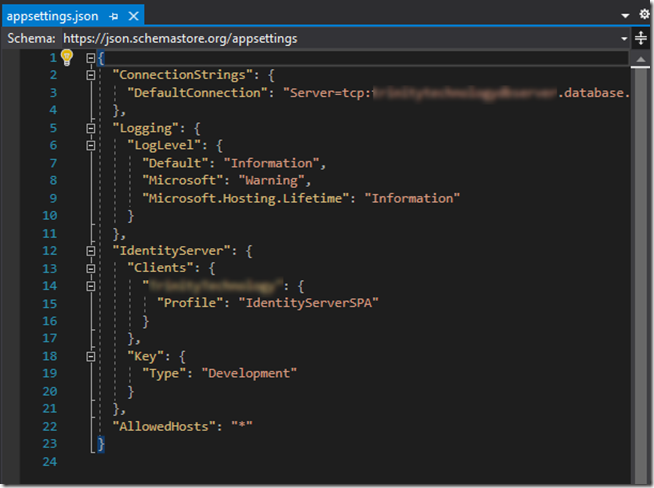
To verify the issue is with identity server configuration you can update the appsettings.json as shown below and redeploy. If the site comes up but you can’t access the default “Fetch data” (see image) then this is the source of your problem; identity server configuration.
in the appsettings.json add the following section:
"Key": {
"Type": "Development"
}
The application will now run [in azure], however this configuration should not be used in a production environment. The following link provides the steps [links] to “Deploy to Azure App Service”
Note: this fix will allow your site to work if you are deploying to Azure [because it is a secure site using https], however if you are trying to deploy to an ISP using http you'll have some more work because http causes error when deployed