
Behind the scenes the “default.aspx” is being searched for; if you put a /default.aspx at the end of the URL you will find that the page will load.
The fix is to go into the site settings and set the “Default Doc” to default.aspx. In my case I had to manually cut the default.aspx from the last position (figure 2) and then paste it above index.aspx. Once I did this the site started working as expected
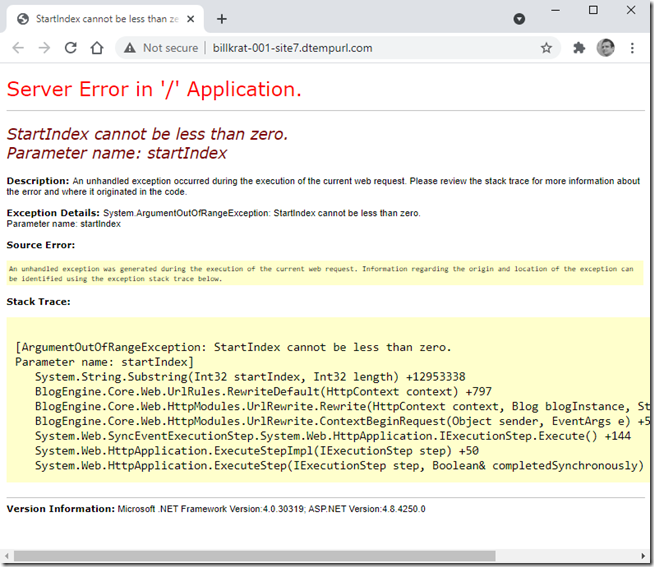
Figure 1.
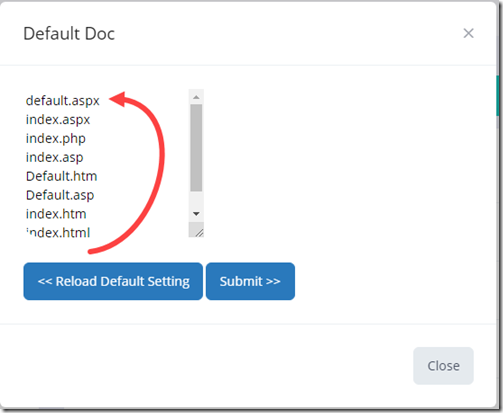
Figure 2.
IdentityServer4.Startup: Information: Starting IdentityServer4 version 4.1.0+5a4433f83e8c6fca7d8979141fa5a92684ad56f6
Exception thrown: 'Newtonsoft.Json.JsonReaderException' in Newtonsoft.Json.dll
Unexpected character encountered while parsing number: �. Path '', line 1, position 1.
You’ll see this error if you are configured with an IdentityServer type=File (figure 1) and your environment is setup to run in “Development”; the fix is to set the ASPNETCORE_ENVIRONMENT=Production (figure 2). Likewise you can leave the setting at “Development” but will have to copy the appsettings.json “IdentityServer” segment to the appsettings.Development.json file (removing the Key type = Development).
In figure 3 and 4 you can see that it gets confused thinking it is in Development expecting JsonConvert to deserialize the contents when in fact the path is our .pfx file. By setting it to Production it ignores the appsettings.Development.json (more closely emulating a production deployed environment which can aid with debugging issues).
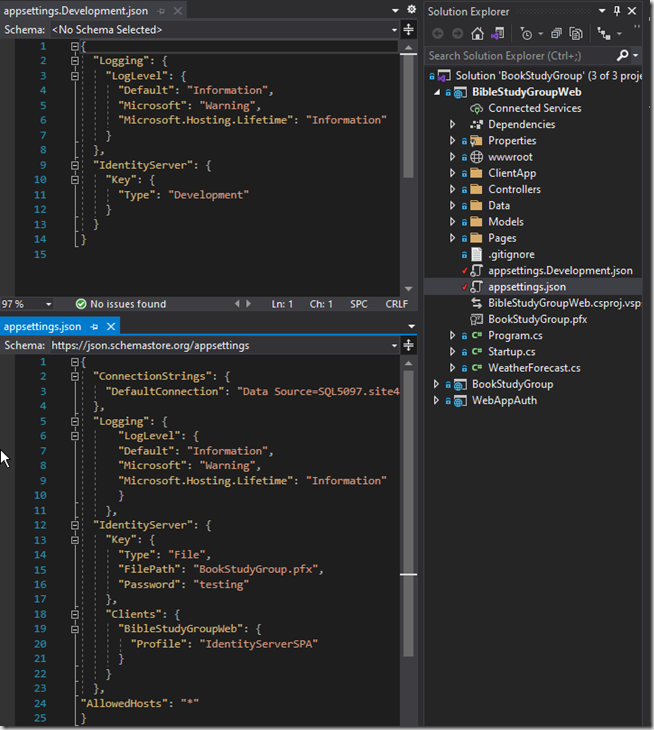
Figure 1.
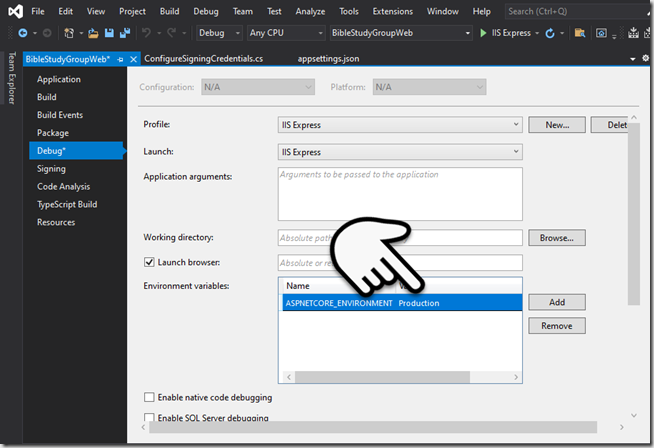
Figure 2.
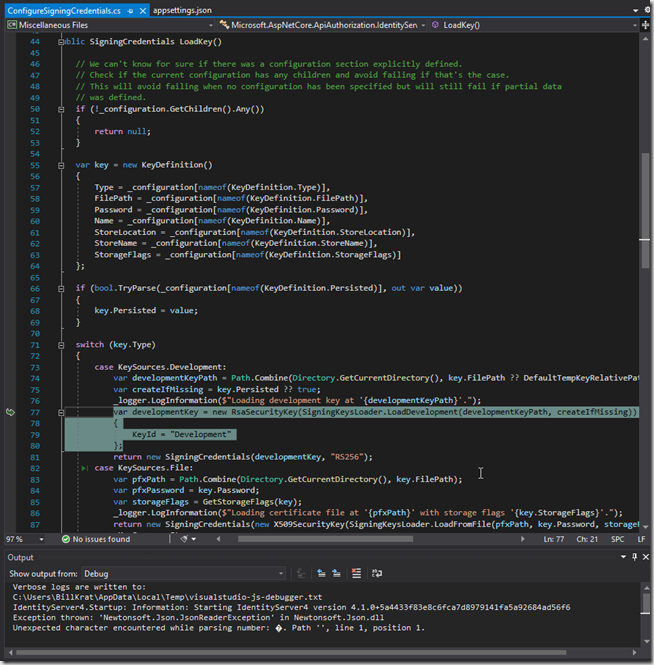
Figure 3.
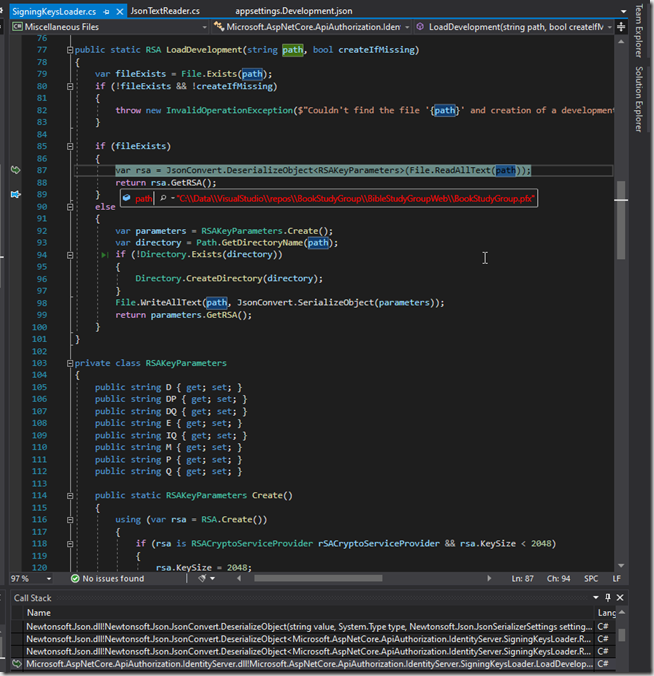
Figure 4.